Ad Fraud
Digital Advertising
.
9 min read
Digital ad fraud is a problem that has a significant impact on the ecosystem and is unlikely to go away anytime soon in this process. Thanks to advancements in verification tools and machine learning technologies, the digital advertising sector is prepared to address this issue.
What is Ad Fraud?
Digital advertising campaigns are best practices when they deliver the appropriate message to the right people in the right place. However, there may be situations in the digital ecosystem where the campaigns aren’t seen and can not reach the targeted audience. Digital ad fraud is the term for any purposeful attempt to defraud digital and programmatic advertising networks and show ads outside of the specified area or audience to profit financially.
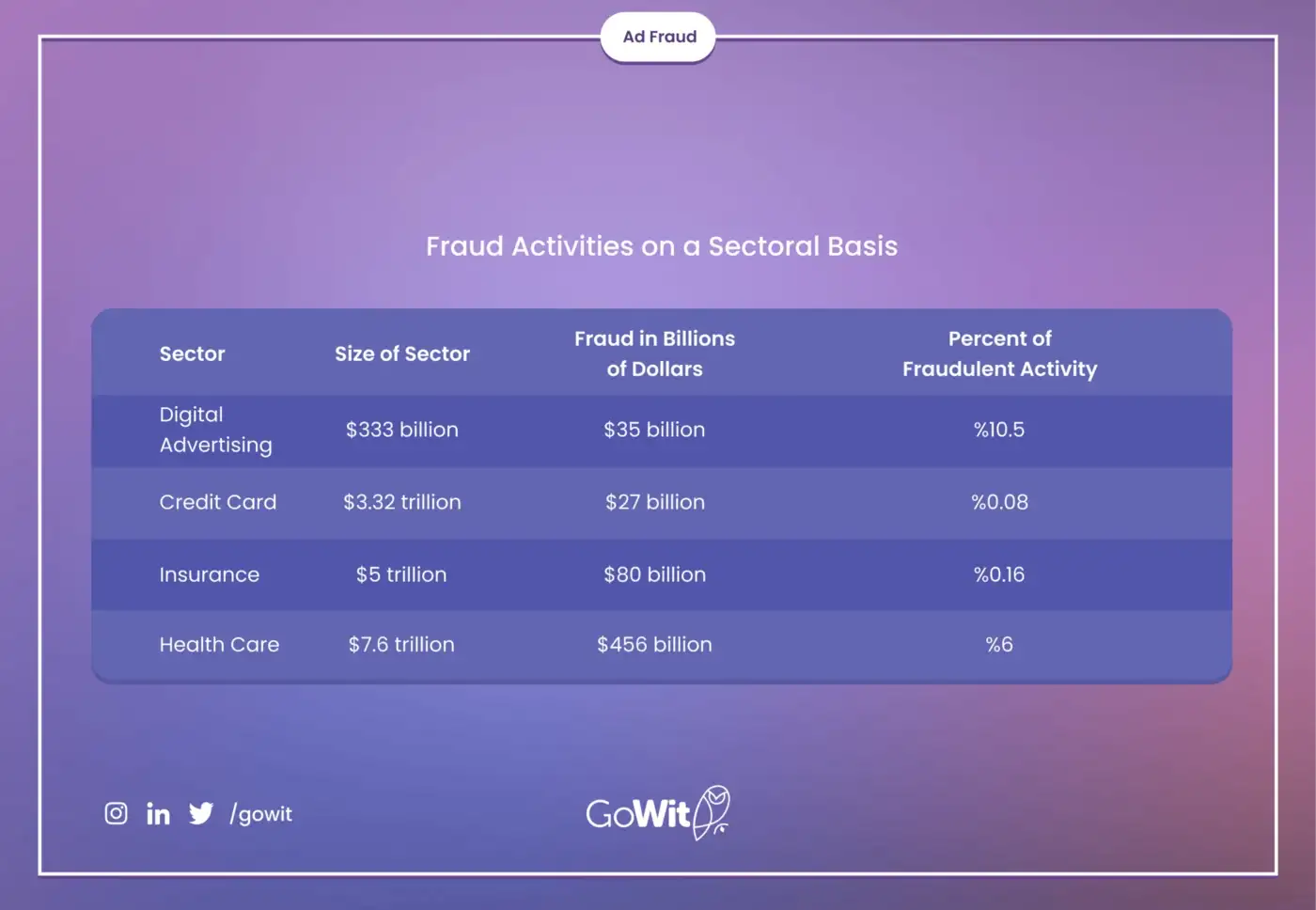
In 2020, global digital advertising annual spending reached 333 billion dollars, with digital ad fraud accounting for 35 billion dollars of that total. Digital advertising fraud has surpassed fraudulent operations in several sectors, including credit cards, health, and insurance, with a rate of 10.5%.
The World Federation of Advertisers (WFA), which represents the world’s top 100 brand owners and 60 advertising organizations, estimates that consumers don’t see 10 to 30% of digital ads and that spending on these ads is a direct source of money for digital ad fraud.
Ad Fraud Techniques
Fraudsters utilize a variety of techniques to deceive advertisers and harm the reputations of both the publisher and the advertiser to gain financial benefit. These are some of the techniques:

Bots
Bots, short for robots, are a type of software that automates some tasks, such as seeing and clicking advertisements and watching movies. Their objective is to make marketers believe that consumers perform desirable behaviors like clicking, viewing, and downloading. Advertisers are charged for impressions and clicks that do not occur.
Click Farm
It is a large community of low-paid workers whose job is to create fake engagement by clicking on ads. The majority of these frauds may be avoided by paying attention to analytics since a significant number of engagements from specific countries might indicate click farms.
Join to get free updates every week
Domain Spoofing
It’s one of the most difficult forms of fraud to identify and avoid, and it’s also one of the most profitable. Fraudsters can manipulate the tags defined by the ad exchange to manipulate advertisers into believing they’re obtaining high-quality inventory when running advertisements on a low-quality website. While impressions and users are real, inventory is misrepresented and hence acquired at a much higher price.
Hiding Ads
It refers to the positioning of advertising on a website in such a way that they are hidden from the user. Even if the user does not see the advertisement, it is counted as an impression.
- Ad Stacking: Multiple advertising on the same inventory is known as ad stacking. Only the top ad shows in the inventory where advertisements are placed with this technique, but all advertisers that have ads in the lower levels of the inventory pay for it.
- Pixel Stuffing: It’s the act of displaying one or more adverts in a 1x1 pixel format. Users generate impressions, but they don’t see the ad.
Ad Injection
Advertisements appear in the inventory without the publisher’s consent or knowledge. These advertisements can take the place of paid ads in inventory or show on sites that are supposed to be ad-free. It’s done by harmful adware add-ons or browser extensions. Both publishers and advertisers are harmed by this technique.
Cookie Stuffing
Cookies are a type of behavior monitoring tool that may be used to figure out which ads resulted in conversions and what users’ interests are. Cookie stuffing occurs when a cookie from a different site than the one they visited is added to the users’ computers without their knowledge. If the user completes a conversion, the website that puts the cookie gets credited for their actions. Furthermore, cookie stuffing may be defined as the loading of multiple cookies into a bot to target them at higher CPM values although they are not high-quality users.
Inventory Arbitrage
It is the technique of acting as ad technology intermediaries to purchase inventory and resell it at a profit. This technique harms the reputation of publishers and forces advertisers to overpay for inventory.
Location Fraud
It happens when advertisers pay to have their ads delivered to consumers in certain areas, but fraudsters send the wrong location, causing the ad to appear somewhere other than where it was meant. Someone surfing the internet on his phone in Rome, for example, could come across advertising for a tour company that organizes travels from Milan to Venice.
User-Agent Spoofing
Every internet request includes a header that contains basic information about the page’s loading location. The browser description is one of these pieces of information. This description is changed in user-agent spoofing to hide information about the browser or to restrict user targeting. Bots who want to mask their trails typically utilize it.
Malicious Apps
They are applications that produce impressions without the user’s knowledge. It can be considered a form of mobile malware.
Cloud Hosting
In-app impressions are seen through cloud-based devices, generating revenue for the app owner. When there is a hacked device in the cloud, fraudsters modify information such as device ID and location, making it look as though there are many devices, namely users.
Bundle ID Spoofing
Fraudsters can deliver an incorrect application identifier to the bidding platform, similar to domain spoofing. This technique prevents contextual targeting and weakens brand security, as well as applications that load advertising through intermediary providers.
Incent Abuse
Incentive-generated user traffic is not in itself a fraud; nevertheless, incentivized traffic is one of the simplest methods to boost installations in a cost-per-download ad campaign. Click-through and conversion rates that are exceptionally high can be used to detect incentive abuse. Fraudsters may stay ahead of this by sending a high number of fake clicks that do not result in a download to lower the conversion rate.
Click Spam
It’s a technique in which fraudsters click even when users don’t and get paid for random downloads. It begins when the user accesses the fraudster’s mobile web page or app. There are several methods. Background clicks by the fraudster outside of the web page’s visible advertisements; clicks by the fraudster while the user is interacting with the application; click at any time due to the presence of an application (memory cleaner, battery performance saver, etc.) running 24/7 on the fraudster’s device.
Click Injection
It’s a more complex type of click spam. It is possible to make an Android app that can identify when other applications are installed on the device. Fraudsters can use this to trigger clicks before the app is installed. As a consequence, the fraudster is compensated for their uploads.
How to detect Ad Fraud?
Digital advertising fraud comes in a variety of forms. Although there is no particular measure that can be used to determine whether or not a company is vulnerable to fraud, there are approaches that can be utilized to gain a better understanding of the issue. The following are a few of these methods.
Increase in Bounce Rates
A significant number of people leaving the site quickly after logging in might be a sign of digital advertising fraud. It’s possible that what appears to be a user is a bot.
Low ROI
If the results from the same campaigns start to deteriorate, the ads may be displayed by bots.
Extreme Increase in Clicks
A spike in clicks on a campaign might indicate that it is being targeted by click farms or bots.
Low Conversion Rates
If conversion rates remain constant as the number of clicks increase, this might be a sign of ad fraud.
Unknown Traffic Sources
Click farms and bots can be detected by an increase in traffic from unknown sites.
Shopping Cart Abandonment
If a high percentage of visitors depart without paying after filling their shopping carts, there may be bots that aren’t completing the purchase.
Depleted Budget
If a lot of money is spent on campaigns but there is no response, it is likely that advertisements aren’t seen because of ad fraud.
Low Session Duration
Bot activity can be detected when users stay on the site for less than one second.
Low Ad Performance
Ad viewability is frequently correlated to the campaign’s success. Even if potential customers search, if the ad has been manipulated by fraudsters, it will not appear and so will not perform.
Low Pageviews
It could be a sign that the ad can’t be displayed for a variety of reasons, including pixel filling or ad stacking in the ad’s current location.
Impressions with no Result
It could mean that the site is being populated by bots and that no attempt is made to increase conversions.
How to Prevent Ad Fraud?
While digital ad fraud is a significant issue that affects all sectors of the advertising ecosystem, certain steps may be taken rather than ignoring a problem that is unlikely to go away anytime soon.
Android and iOS App Installation Verification
When any true installation information can’t be identified, the interaction is stopped.
Monitoring Geographical Values
Click spam can be identified by the geographic distance between the click and the associated install. When the distance between the click and the install site exceeds the defined value, installs are marked as geographical outliers and attribution is disabled.
Tracking Click-Download Durations
If the period between an ad click and download is too short, it’s a sign that scammers used click injection to install the software.
Blacklisting
Verification providers utilize algorithms to identify suspected fraudulent sites and apps in fraud practices like click-farming and invalid user traffic. In these systems, data scientists examine apps and websites using a range of experimental, technical, and non-technical models to determine if there is evidence of non-human activity or display manipulation. Data scientists analyze publishers’ records, privacy rules, and other paperwork in addition to automated analyses. The site or application will be blacklisted if evidence of fraud is discovered after all of these examinations. Bots, known fake sites, and data centers that are listed across the industry can also be utilized to avoid fraudulent user traffic and digital ad fraud.
IP Blocking
Validation providers capture the IP address where the ad was served and match it to data center listings using various algorithms for non-human produced traffic. The next step is to stop the source of the fraudulent activity once it has been discovered. The scammer’s access will be limited using this way.
Avoiding Excessive Interaction
An abnormally high amount of clicks from a single source may be click spam. As a result, when the number of install-related clicks exceeds the set threshold, attribution is disabled.
Using the Ads.txt, App-ads.txt, Sellers.json, and Buyers.json Standards
To prevent fraudulent activity, publishers and platforms such as SSP, DSP, and ad exchange can publish files like ads.txt, app-ads.txt, sellers.json, and buyers.json on their sites. While these measures will not be able to avoid all of the above-mentioned fraudulent approaches, they will increase transparency, making fraudulent operations more difficult and increasing reliability. According to research, 44% of the sites in Alexa’s top 1000 list publish ads.txt files.
Conclusion
With the rapid advancement of digital advertising technologies, the amount of money spent on it is increasing. Digital ad fraud is a problem that has a significant impact on the ecosystem and is unlikely to go away anytime soon in this process. Thanks to advancements in verification tools and machine learning technologies, the digital advertising sector is prepared to address this issue. In the face of this challenge, publishers that are targets of digital advertising fraud, as well as platforms such as SSPs, DSPs, and ad exchanges, should benefit from the technology and standards that safeguard them.
Share
